Generate Ssh Key In Windows Powershell
- Generate Ssh Key In Windows Powershell 7
- Powershell Command To Generate Ssh Key
- Generate Rsa Key Powershell
Overview
PowerShell remoting normally uses WinRM for connection negotiation and data transport. SSH is nowavailable for Linux and Windows platforms and allows true multiplatform PowerShell remoting.
To generate an SSH key in Windows 10: Ensure the Windows 10 OpenSSH client is installed. Run “ssh-keygen” in Command Prompt and follow the instructions to generate your key. Applies to Windows 10. Sep 26, 2019 To generate an SSH key with PuTTYgen, follow these steps: Open the PuTTYgen program. For Type of key to generate, select SSH-2 RSA. Click the Generate button. Move your mouse in the area below the progress bar. When the progress bar is full, PuTTYgen generates your key pair. Type a passphrase in the Key passphrase field. Mar 19, 2019 How to make Git, SSH and PowerShell dance together in Windows 10 Today I setup a new Windows 10 laptop. After struggling to get SSH working with Git in PowerShell, I figured it was a good idea to record the process for next time.
Since ssh-copy-id isn’t implemented on the OpenSSH port for Windows (because it’s a bash script), I wanted to replicate that functionality so that I could easily copy ssh user keys to systems, consistently and easily. So I implemented this functionality as PowerShell. The SSH server must be configured to create an SSH subsystem to host a PowerShell process on the remote computer. And, you must enable password or key-based authentication. Set up on a Windows computer. Install the latest version of PowerShell, see Installing PowerShell Core on Windows. Apr 19, 2019 How to generate SSH keys in OpenSSH for Windows 10 Install the OpenSSH module for PowerShell. Generate user key pair. In PowerShell, change directories to the path above where. Copying the public key securely. The OpenSSH tools include the SCP and SFTP utilities.
Generate Ssh Key In Windows Powershell 7
WinRM provides a robust hosting model for PowerShell remote sessions. SSH-based remoting doesn'tcurrently support remote endpoint configuration and Just Enough Administration (JEA).
SSH remoting lets you do basic PowerShell session remoting between Windows and Linux computers. SSHremoting creates a PowerShell host process on the target computer as an SSH subsystem. Eventuallywe'll implement a general hosting model, similar to WinRM, to support endpoint configuration andJEA.
The New-PSSession, Enter-PSSession, and Invoke-Command cmdlets now have a new parameter set tosupport this new remoting connection.
To create a remote session, you specify the target computer with the HostName parameter andprovide the user name with UserName. When running the cmdlets interactively, you're prompted for apassword. You can also, use SSH key authentication using a private key file with the KeyFilePathparameter.
General setup information
Powershell Command To Generate Ssh Key
PowerShell 6 or higher, and SSH must be installed on all computers. Install both the SSH client(ssh.exe) and server (sshd.exe) so that you can remote to and from the computers. OpenSSH forWindows is now available in Windows 10 build 1809 and Windows Server 2019. For more information, seeManage Windows with OpenSSH. For Linux,install SSH, including sshd server, that's appropriate for your platform. You also need to installPowerShell from GitHub to get the SSH remoting feature. The SSH server must be configured to createan SSH subsystem to host a PowerShell process on the remote computer. And, you must enablepassword or key-based authentication.
Set up on a Windows computer
Install the latest version of PowerShell, see Installing PowerShell Core on Windows.
You can confirm that PowerShell has SSH remoting support by listing the
New-PSSessionparametersets. You'll notice there are parameter set names that begin with SSH. Those parameter setsinclude SSH parameters.Install the latest Win32 OpenSSH. For installation instructions, see Getting started with OpenSSH.
Note
If you want to set PowerShell as the default shell for OpenSSH, seeConfiguring Windows for OpenSSH.
Edit the
sshd_configfile located at$env:ProgramDatassh.Make sure password authentication is enabled:
Create the SSH subsystem that hosts a PowerShell process on the remote computer:
Note
You must use the 8.3 short name for any file paths that contain spaces. There's a bug inOpenSSH for Windows that prevents spaces from working in subsystem executable paths. For moreinformation, see this GitHub issue.
The 8.3 short name for the
Program Filesfolder in Windows is usuallyProgra~1. However,you can use the following command to make sure:Optionally, enable key authentication:
For more information, see Managing OpenSSH Keys.
Restart the sshd service.
Add the path where OpenSSH is installed to your Path environment variable. For example,
C:Program FilesOpenSSH. This entry allows for thessh.exeto be found.
Set up on an Ubuntu 16.04 Linux computer
Install the latest version of PowerShell, seeInstalling PowerShell Core on Linux.
Install Ubuntu OpenSSH Server.
Edit the
sshd_configfile at location/etc/ssh.Make sure password authentication is enabled:
Add a PowerShell subsystem entry:
Optionally, enable key authentication:
Restart the sshd service.
Set up on a macOS computer
Install the latest version of PowerShell, see Installing PowerShell Core on macOS.
Make sure SSH Remoting is enabled by following these steps:
- Open
System Preferences. - Click on
Sharing. - Check
Remote Loginto setRemote Login: On. - Allow access to the appropriate users.
- Open
Edit the
sshd_configfile at location/private/etc/ssh/sshd_config.Use a text editor such as nano:
Make sure password authentication is enabled: Generate key hash android facebook windows 10.
Add a PowerShell subsystem entry:
Optionally, enable key authentication:
Restart the sshd service.
Authentication
PowerShell remoting over SSH relies on the authentication exchange between the SSH client and SSHservice and doesn't implement any authentication schemes itself. The result is that any configuredauthentication schemes including multi-factor authentication are handled by SSH and independent ofPowerShell. For example, you can configure the SSH service to require public key authentication anda one-time password for added security. Configuration of multi-factor authentication is outside thescope of this documentation. Refer to documentation for SSH on how to correctly configuremulti-factor authentication and validate it works outside of PowerShell before attempting to use itwith PowerShell remoting.
Generate Rsa Key Powershell
PowerShell remoting example
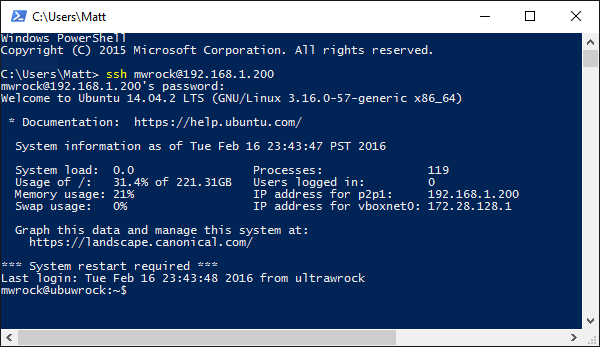
The easiest way to test remoting is to try it on a single computer. In this example, we create aremote session back to the same Linux computer. We're using PowerShell cmdlets interactively so wesee prompts from SSH asking to verify the host computer and prompting for a password. You can do thesame thing on a Windows computer to ensure remoting is working. Then, remote between computers bychanging the host name.
Known issues
The sudo command doesn't work in a remote session to a Linux computer.
See also
Login With Password
- Workgroup users
ssh user@host
- Domain users: Prior to v7.7.0.0, domain needs to be explicitly specified. Any of the following formats work
ssh -l user@domain hostssh domainuser@hostssh user@domain@hostssh user@host(works from v7.7.0.0 onwards provideduserhas no conflicts otherwise - ex.userexists both on local account data base and on domain)
Login With SSH Keys
Usage from client-side (ssh)
- Generate a key pair on the client (preferably with a passphrase):
ssh-keygen -t rsa -f id_rsa
- Register private key with ssh-agent (optional, for single sign-on experience)
net start ssh-agentssh-add id_rsa
- Login using private key
ssh -i .id_rsa user@host(workgroup user)ssh -i .id_rsa -l user@domain host(domain user)
Setup server-side (sshd)
- Append contents of
id_rsa.pub(client's public key) to the following file in corresponding user's directory%systemdrive%Users<user>.sshauthorized_keys(create one if needed). - Double check access permissions on authorized_keys (only System, Administrators and owner can have access).
icacls %systemdrive%Users<user>.sshauthorized_keys
Login using Kerberos Authentication
Setup server-side
- On a domain joined server, set GSSAPIAuthentication to
yesin sshd_config
Usage on a domain joined Windows client logged in as domain user
ssh -K host
Please note you have to use the hostname instead of the username.
For Unix and Linux users
The Modern Unix Rosetta Stone includes PowerShell examples of common Unix and Linux commands.